MS Office documentation system provides great convenience to the day-to-day running of office ever since its invention. Now processing business files are no long limited in the office spot, with the development of smart digital products, people can easily reach their documents in a smart phone or newly released tablet any where they want. Regardless these advantages and convenience office documentation system offer us, how to copy protect the content of files is an urgent question need to be solved.
Office documents in a USB drive disc need protection. USB drives are easily lost which gives the bay guy a chance to get your valuable private information or business ideas. To prevent office word, excel, PPT in USB disks being copied illegally you can refer to USB Copy Protection.USB Copy Protection specialized in providing office copy protection, which includes excel copy protection, word copy protection and power point copy protection, and copy protecting other picture, audio and video files in portable USB storage devices.
Click on the following button to download USB Copy Protection and experience the performance in copy protecting your office documents on Windows 7/ Windows 8/XP
Table of Contents
Step 1 Plug in Your USB Disk and Install USB Copy Protection
Plug your USB drive disk into a computer with Windows 7/ Windows 8/XP system, open the exe program you’ve downloaded, and then install it according to Setup Wizard.
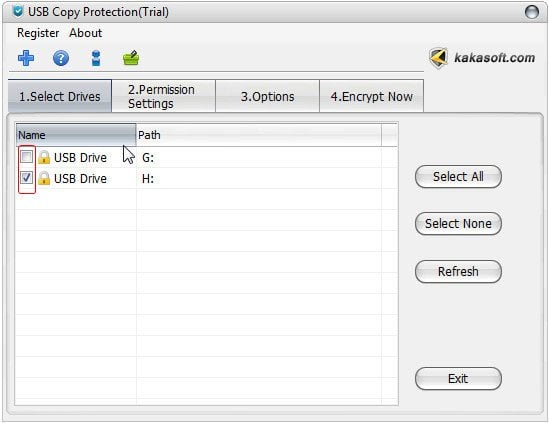
Step 2 Choose a Drive to Copy Protect
To start USB docx copy protection and copy protection of other files, you are required to double click “USB Copy Protection” inconstant on the desktop, then select “Select Drives” option, and navigate to the copy protection list and check the drive you wish to protect.
If your drive not exists on the list please check your USB drive and then click on “Refresh”.
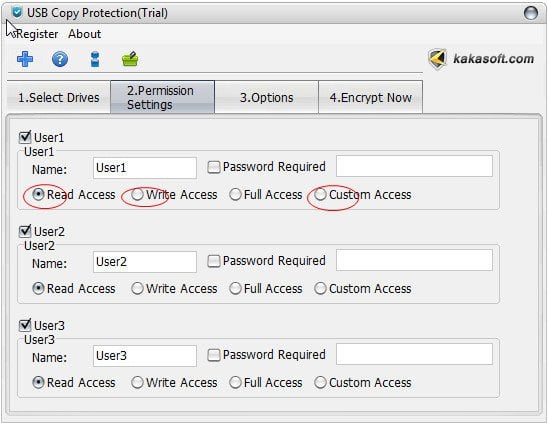
Step 3 Make Settings and Assign Permissions
To ensure ppt copy protection and .docx copy protection, navigate to “Permission Settings”, here you can assign different access permissions to different users, or customize access rights on “Custom Access”.
Able/ prohibit up to 15 kinds of access right, limit access expiration date, access IP, display files in specific formats.
ONLY the Admin has full access to all files in the disk which ensure total control and supervision of all files contents.
Step 4 Select Security Level
To safeguard word copy protection and excel copy protection, you can select different security level according to you requirement.
In “Options” option you can add some personalized features to the protection of USB Copy Protection, you can choose a security level, or a special icon, rename the program or rename the client.
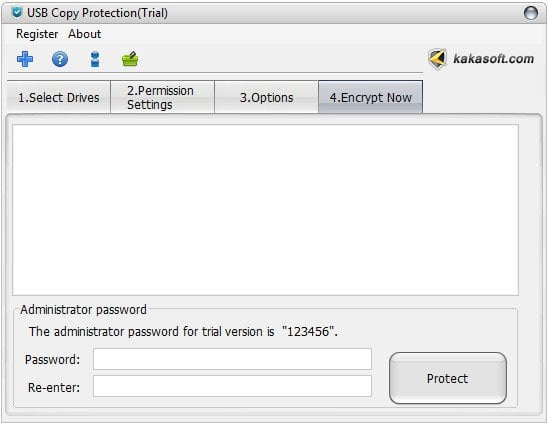
Step 5 Enter Password and Finish Copy Protection
To ensure powerpoint copy protection and set Admin password for your copy protection, click on “Encrypt Now” option, if you are using a trial version please put in 123456, and confirm it. Next, click “Protect”.
Tips:
- If you want to access to office documents in your USB flash drive, you need to open your disk and then run the client program in it. Log in as the Admin and enter the password. Then in the document management window you can do any modification on hatchling files.
- Once you’ve finished copy protecting your USB drive you will find all files and documents are hidden and protected, and the only way to access them is through the client.
- USB Copy Protection support copy protection on all kinds of portable USB drives, namely USB flash drive, pen drive, memory stick, SD card, TF card, HDD drive etc.
- Copyright protection means a lot for people with intellectual properties and educational materials.
Copy protection on Windows 7 and Windows 8 is a highlighted feature for USB Copy Protection, and you will never find such a reliable and stable software in the market if you miss this one!