USB Security – Download USB Disk Security to Protect USB Drives
Lock, encrypt, password protect USB flash drive, thumb drive, pen drive, memory stick, and other portable storage devices.
Password Protect USB flash drive, pen drive, memory card, thumb drive, etc.
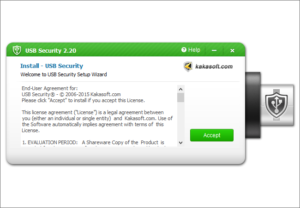
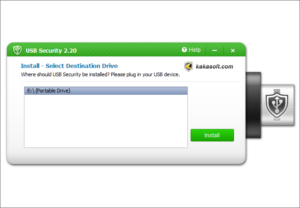
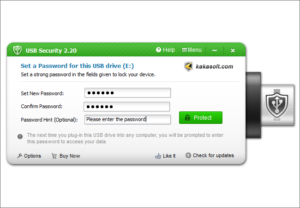
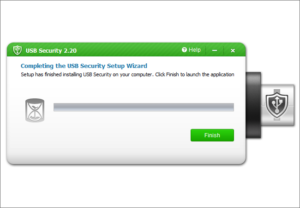
Lock your USB drive in 3 simple steps.
Protect your files automatically after the USB disk plugs into a PC.
Enjoy protection anytime and anyplace without installation.
Lock and unlock USB drives on any computer without installation.
File Size: 1.5MB
Version: 3.0
Updated: Nov 27,2021
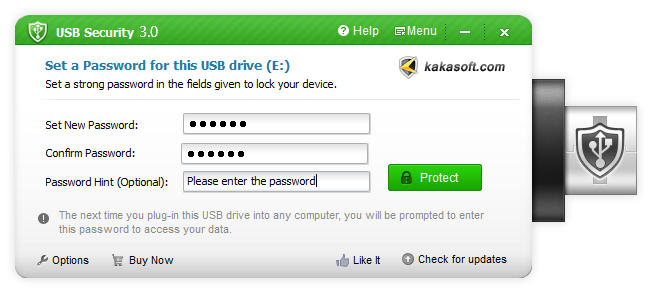
How to Lock USB Drives with USB Disk Security?
USB Disk Security well protects your sensitive information in USB drives with the strongest encryption technique.
What Make USB Disk Security Stand Out?
This USB disk security program ensures comprehensive data security of your confidential data on your USB flash drives.
Reliability
Ensure data security in USB flash drives with multiple layers of protection and advanced encryption technique. Password protects all types of external USB storage devices.
Ease of Use
Lock data in a USB disk in 3 simple steps. You can access the protection of USB Security freely on any computer without installing it again.
Instant Protection
Support AutoPlay protection feature when the disk is connected to PC. You can ensure data security in a USB drive and access confidential documents as soon as they are plugged in.
Virtual Drive
It mounts protected USB disks to a virtual drive so that you can safely check or modify protected files. It avoids the risk of preventing USB viruses and unlocking data protection.
Zero Malware Violating
Prevent your data in USB drives from being eavesdropped on or invaded by malware or cybercriminals and be able to block any unauthorized access.
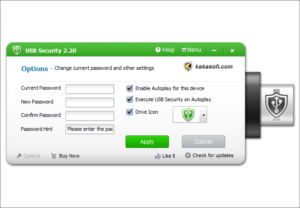
Password Hint
Offer a special password hint feature that allows you to restore passwords when you forget them by accident.
Powerful USB Security protection software
Sensitive and valuable data needs urgent protection. With feature-rich USB Security you can secure the external drive as a whole and supports password-protecting USB flash drive, HDD hard drive, thumb drive, pen drive, memory stick, memory card, and all other portable storage devices in the Windows system
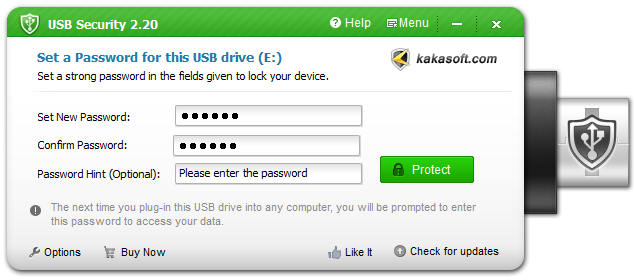
USB Encryption within a Few Clicks
Once locked files in a USB flash drive, you can access the file beyond the limitation of time and place.
FAQs of USB Security
All people who need use USB and other portable devices in either local PC, LAN, Network or public places. You might share PC with other users in the same computer and forget unplug your USB drive. You might check emails or process job files in a coffee or airport waiting room. You might lose your USB drive with important, private or sensitive data. This USB disk security program will secure USB and prevent data leaking and unauthorized access to your USB drives and all other portable devices.
Notice: There isn’t any “backdoor” in USB Disk Security. if you have forgotten your password,YOU WILL NOT BE ABLE TO UNPROTECT YOUR USB DRIVES. Please make sure that you remember your password at ALL times or keep it in a safe place.
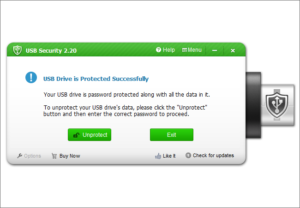
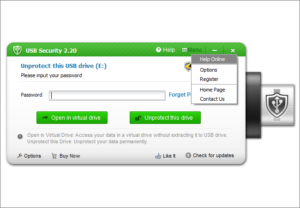
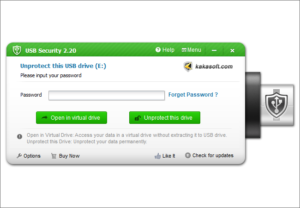
Simply launch the program from your protected USB drive and input your password to unprotect it. USB Security offers you two different methods to access your protected data.
Open in Virtual Drive: Access your data in a virtual drive without extracting it to USB drive.
Unprotect this Drive: Unprotect your data permanently.
Simply download the USB Security from our website. Run the setup again and install the program on your USB flash drive in which you have protected your data and then unprotect your data by entering correct password.
Yes. This USB Security software allows you to protect any media that you can read and write to: USB drive, Flash drive, thumb drive, jump drive, memory card, memory stick, external hard disk, floppy, Firewire portable drives, etc.
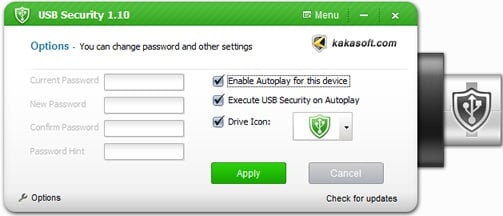
Yes. Run the program and enter your password, click ‘Options’ where you find two options: 1. Enable Autoplay for This Device 2.Execute USB Secure on Auto play. To disable Auto play feature unchecked these boxes and click ‘Apply’ to finish.
You can change your password any time you want. Simply Click ‘Options’ and you will see a password set filed, simply enter your previously set password and then set and confirm a new password. To finish click ‘Apply’.
Yes. USB Disk Security is compatible with Windows 10/8/7/Vista/2003/XP/2000,32&64 bit.
No, the encrypted USB flash drive cannot be read on Mac, so the user cannot copy the encrypted file.
It is shareware but free download and trial is available. You can evaluate most features without paying.
We strongly recommend you to try USB Security first before purchasing. We don’t need your money as much as we need your satisfaction. If you are happy with it, then pay us and register.
Registered users will get full license uses of the program, no functionality limits. And we provide 24*7 life-time priority customer support for every registered user.
A single-user license allows the program to be run on ONE USB drive only.
Yes, we offer special discount licenses for all types of organizations and academic institutions.
Yes. We offer 24*7 free customer support for all our users. If you have questions or comments about USB Security, free free to contact us via support@kakasoft.com .
We give high priority to our customers’ suggestions for future versions of our software. If you have a feature request, be sure your copy is registered and free to send us an email.
Do not worry about upgrade. All your data and settings are reserved after each upgrade. And usually upgrades are free for registered users.
Click the registration menu on the main window of the software, and then enter the registration code. Learn More
What People Are Saying

Great software, I must say USB Security protected my files very well. Highly recommended!!!
– Fred

This software is outstanding protection. I am happy with my decision to give it a shot. Recommended!
– Charles

It is a good software for protection. Most of my files are sensitive. So, in case of any mishap, I wanted my files to be inaccessible and this service served the purpose. Glad to use it.
– Alice

Amazing software to protect your files on the pen drive. My experience was great. I have a pen drive password protected by this. And a few days ago I need to access a file saved in it. But unfortunately, I forgot the password, and the hint feature helped me to recover it. Anyway, this software keeps the pen drives secured that long and its hint feature is cool. Loved it.
– Alice